这个题目搭建环境不知道怎么搭建…控制不好权限直接就可以执行命令拿flag了..
改一下函数, system和/bin/sh 或者给出libc地址? gift
gcc -o race main.c -fno-stack-protector -no-pie需要关闭canary和pie
https://bbs.huaweicloud.com/blogs/399812
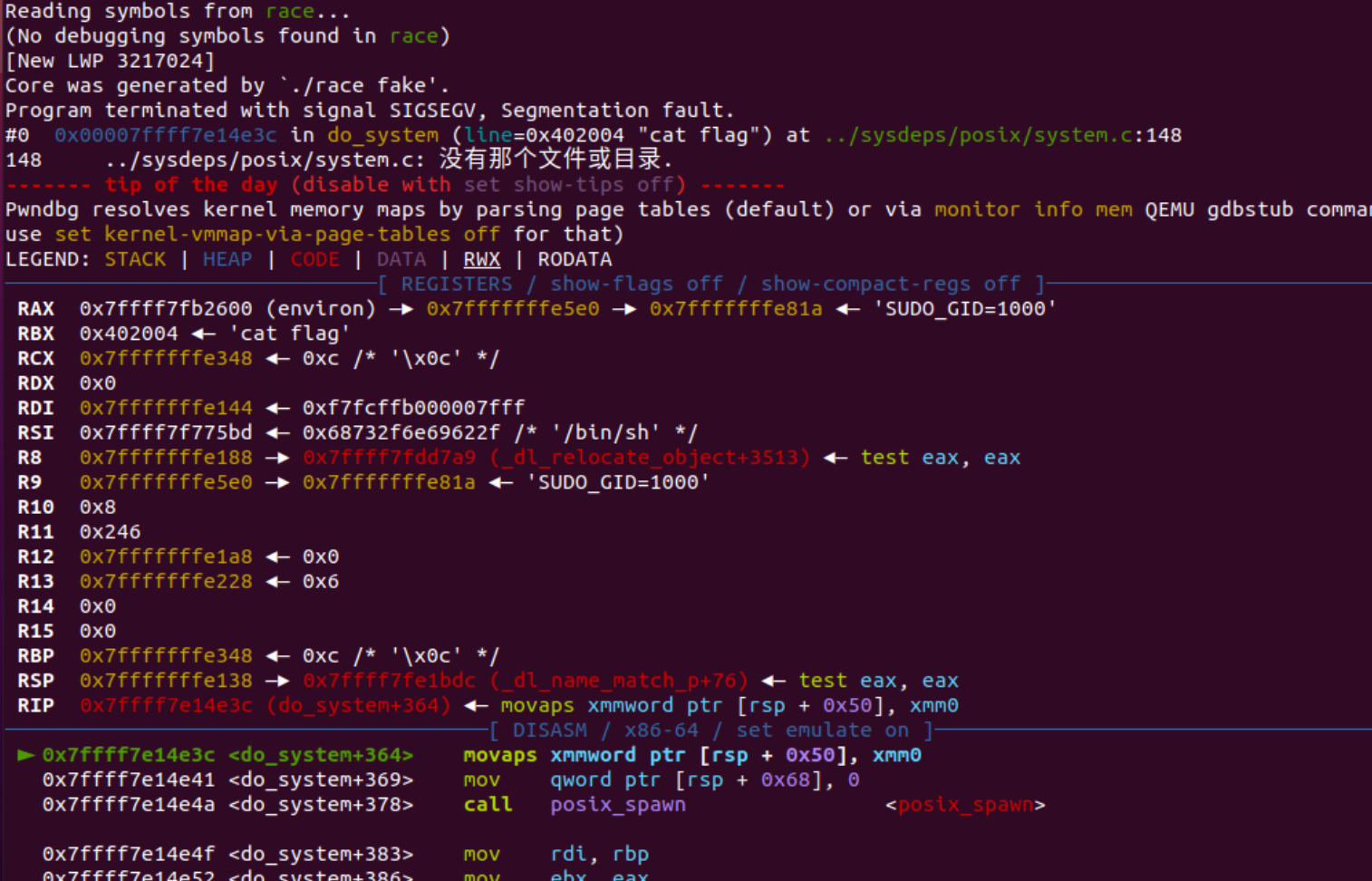
为啥出错呢, core dumped看一下吧
https://blog.csdn.net/qq_43714097/article/details/130734858
https://stackoverflow.com/questions/32892908/c-system-raises-enomem
https://airman604.medium.com/protostar-stack7-walkthrough-2aa2428be3e0
https://blog.csdn.net/weixin_44411509/article/details/109860791
https://blog.csdn.net/chichoxian/article/details/53486131
主要就是这里说的问题
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
| #include <fcntl.h>
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <sys/stat.h>
#include <unistd.h>
char *argv[]={"cat","./flag", NULL};
char *envp[]={0,NULL};
void showflag() { execve("/bin/cat",argv,envp); }
void vuln(char *file, char *buf) {
int number;
int index = 0;
int fd = open(file, O_RDONLY);
if (fd == -1) {
perror("open file failed!!");
return;
}
while (1) {
number = read(fd, buf + index, 128);
if (number <= 0) {
break;
}
index += number;
}
buf[index + 1] = '\x00';
}
void check(char *file) {
struct stat tmp;
if (strcmp(file, "flag") == 0) {
puts("file can not be flag!!");
exit(0);
}
stat(file, &tmp);
if (tmp.st_size > 255) {
puts("file size is too large!!");
exit(0);
}
}
int main(int argc, char *argv[argc]) {
char buf[256];
if (argc == 2) {
check(argv[1]);
vuln(argv[1], buf);
} else {
puts("Usage ./prog <filename>");
}
return 0;
}
|
回头整理一下搭建题目环境。。。